Succesful pentest of the Thinkwise Platform
It is important to us as Thinkwise that our customers have a secure Low Code software platform. That is why we periodically do a pentest to prove that the Thinkwise Low Code platform is sufficiently safe.
The pentest was augmented with several audit activities, in which security controls, secure configuration and secure development were discussed in interview form. The following topics were covered in this audit:
- Secure design and architecture (both network and application-level)
- Secure software development (SAST, DAST, threat modelling etc.)
- IT Security Controls: authorization, authentication, password management
- IT Security Controls: secure communication and encryption; data protection at rest
- IT Security Controls: access control / default deny
Description of test scope
Because the attack surface of applications built using the Thinkwise low code platform is defined by the components available at runtime, the pentest was performed using an example application (the “Insights” application).
The attack surface (areas of the information system that an attacker or security evaluator can choose to initiate an attack) for the pentest was defined as, and limited to:
- The Thinkwise Insights application
- The OpenID implementation on the Thinkwise Insights application
- Indicium + Universal
In addition to the attack surface defined above, the testers also received VPN access to the server hosting the frontend and indicium components.
Test approach, methodology and process
For the test, the testers received three test accounts for the Insights application, each with different access rights, so that proper tests for access control could take place. As such, the pentest was executed grey box. The test was originally planned to be performed in 32 hours of effective testing, spread over 5 working days.
The testers also received credentials for testing OpenID (client ID and client secret) and credentials for connecting through VPN.
Reconnaissance for the pentest was performed with industry-standard tooling (scanners and scripts) and by manually searching through publicly available sources. At network level also open ports and active services were investigated.
During the execution- and exploitation phase various tools were used. However, the majority of the checks were performed manually, where internet traffic was investigated and manipulated with proxy tooling.
The OWASP top 10 was the base for the performed interactive checks on application level. The test was executed in line with ASVS level 2 guidelines, using two testers with at least two relevant security testing certifications.
Description of outcomes
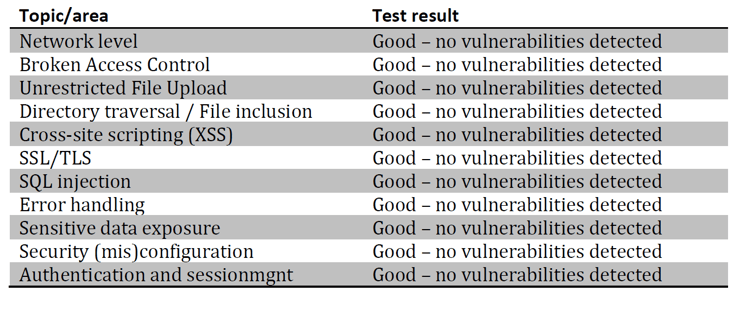
During the pentest on the Insights application, the testers have not succeeded in breaching data or taking control of the server; this is already a good result. Also, most findings were related to webserver configuration, and therefore are specific to the Insights application and not applicable to the Thinkwise platform in general.
After the initial pentest was performed, findings were addressed by Thinkwise and were then retested by nSEC/Resilience. After this retest (and at the time of writing this document) no findings remained open.
Even taking into account that all pentest describe the security of the system under test at a specific moment in time and that security testing should always be seen as a continuous process, the testers do not see any vulnerabilities in the application (platform) at this point, which is a very positive result.
Presented per category (based on OWASP categories):
You can download the full report here.